
Exam Proctor is a proctor-assistance system that essentially automates a proctor being present nearby and casually observing your screen activity. The system also provides a clear record of the activity by recording screenshots; this occurs only when activity is detected for review by a proctor. Students who simply observe the exam rules have no need to be concerned.
The system watches the screen, network and processes for activities related to known avenues of cheating or that are otherwise atypical. Only the detection of unusual activity will trigger a series of screenshots. Proctors are alerted in real-time to evaluate such anomalies to see if the recorded activity warrants a concern and may remotely request additional screen shots.
After the exam, proctors will review the screenshots and other meta data. And where there is clear justification, may use this as evidence of academic misconduct under Policy 71.
Screenshots are held securely and are deleted from the server after one month; access is restricted to the course instructor, proctors, Director of Academic Integrity, Associate Deans and Engineering Computing personnel. Where disciplinary action is taken, the Associate Dean may retain copies of screenshots for longer according to the requirements of that process.
As of late 2025, Microsoft Edge browser and Microsoft CoPilot offer AI assistance to users. To avoid the temptation to use these extensions, both Edge and CoPilot are disabled for the duration of the exam.
This has an unfortunate ramification: some applications may use Edge to display online help files inside the application. Sometimes it will always use Edge, other applicaitons will use the user’s defined default browser, which may be Edge.
|
Tip
|
This could make application online help unavailable for some or all students. |
No student-directed accusations should take place during the exam as that would upset other students trying to concentrate on their work.
Some incriminating situations may be beyond the student’s control. For example, on some workstations, innocently pressing Alt-Spacebar will sometimes bring up Microsoft Co-Pilot AI Assistant. Or a growing number of applications will have an AI extension that can be unintentionally activated by an errant key press. The intent of the screenshot is to give clear context… is the student actively using the AI tool?
Internally, the system notes how long each on-screen tool is active. Someone who accidentally invokes a forbidden application but obviously closes it too quickly to have used it maliciously, should be given the benefit of the doubt.
Exam Proctor presents a simplified version of information collected, much like a first order approximation which is helpful but not necessarily definitive. Engineering Computing will have still more detailed system logs and specialized knowledge which can be used by its staff to corroborate the evidence given to faculty, or perhaps support the student perspective if there is a disagreement about what actually transpired. While a screenshot is quite strong evidence there may have been cheating, any decision to pursue a policy-level academic offence based on it must first get a review of the exact details by Engineering Computing to ensure the results are a fair interpretation of the events.
Have the students sign in normally. Many logins will include auto-start applications which the student should then close - like sometimes Teams, Email, etc. We won’t start monitoring until the room has quieted down and students have closed all non-exam materials.
Once the room has settled, start the tool from the podium computer at the front of the classroom, and tell it to start the exam.
Have the instructor or proctor, on the podium computer, do the following:
Turn off the overhead projector - so students doen’t see the podium screen
Visit the URL http://tuque.uwaterloo.ca/classblock
Enter the exam details (professor, exam end time) and indicate to start monitoring
Leave the web page running for the duration of the exam - you need not worry about the screen contents, the processes are automated.
click URLs and monitor the screen 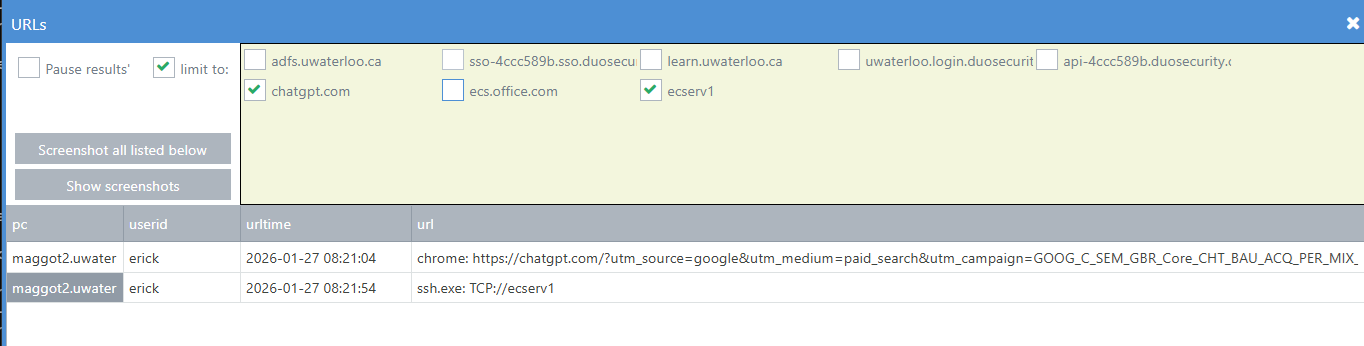
select "limit to" and then select any questionable hostnames to see who has had them active, listing userids and URLs below.
press "Screenshot all listed below" to take screen shots of those with suspicious URLs open
Following the Exam, contact Erick for a review of the collected data. It will include a detailed list of screen transaction, and when suspicious activity was noted: screenshots with the user’s name, workstation name and time.
Updated October 20, 2025